2025 is fast approaching and extortion and ransomware groups cease to be a threat in the global cybersecurity space. While the most prominent threat actors – Lockbit, Play, and Ransomhub – have dominated the area in the last few years, new groups continue to emerge.
One of these groups that has popped up fairly recently, Kairos, has claimed attribution for several breaches in the past month alone, and it appears that they have only been active within the past year based off of the data that I’ve been able to gather. According to their DLS (Dedicated Leak Site), they have breached 14 companies so far; several of the businesses are health-care related but there appears to be no strict targeting based on a particular business sector.

Based off of their Rules page and their main listing, they generally give a week for companies to respond to their extortion threat, after which they will then publish the data they have been able to exfiltrate.
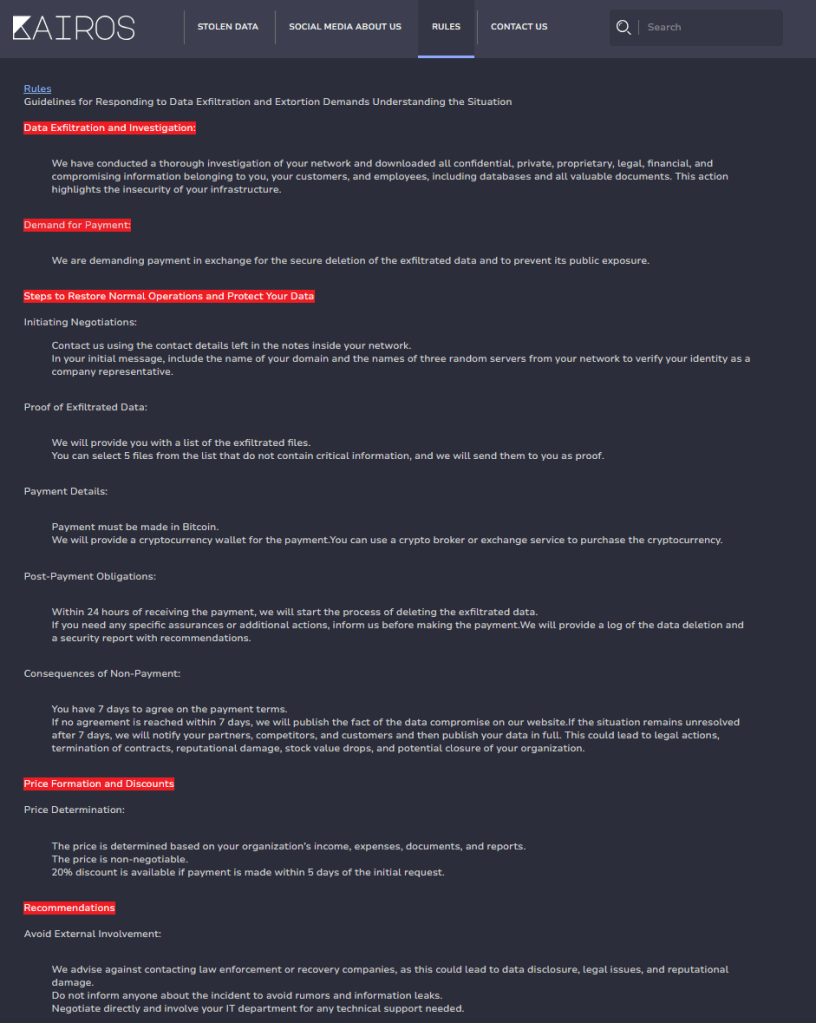
Two of the listed companies, Clay Platte Family Medicine and Physical Medicine & Rehabilitation Center, have both published breach notices indicating that both companies discovered that they were breached several months before the DLS listing was posted, on June, 6 2024 and July, 8 2024 respectively. This would seem to indicate that Kairos has been active for several months, and based off of this time frame – when the data ends up being published several months after the initial breach, I would wager we will be seeing more DLS postings soon.
According to Cyjax, Kairos started a bid on an IAB (initial access broker) listing for a Canadian construction company, but didn’t seem to actually follow through on the bid as the listing was reposted. While they never finished their purchase attempt, having access to an IAB would increase the scope in which Kairos could operate. Cyjax also found an interaction in another Russian-language cybercriminal forum in which a user “Secdat9xx” indicates that Kairos is another handle they use on Tox.
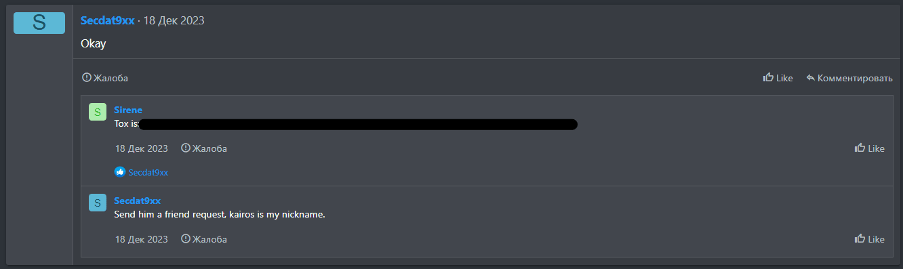
Source: Cyjax
There is not enough information to accurately relate Secdat9xx with Kairos, but if any techniques that Secdat9xx was associated with were found to be used in any Kairos-related extortion events it would paint a clearer picture.
The same user posted 2 guides on RAMP, another Russian speaking cybercrime forum. One of these guides gave details regarding the use of a post-explotation script called “DarkSilent” to help obfuscate persistence, and another discussing a method to utilize ZeroLogOn (CVE-2020-1472) to scan and access vulnerable active directory servers.
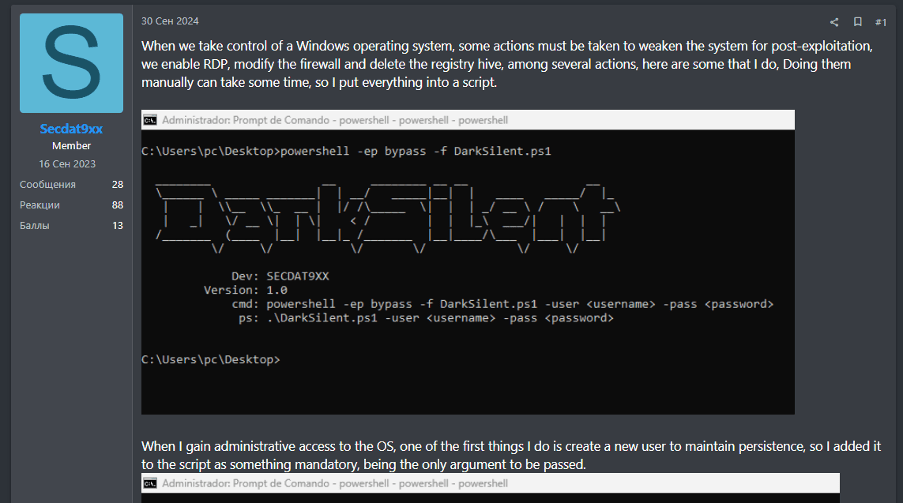
Source: Cyjax
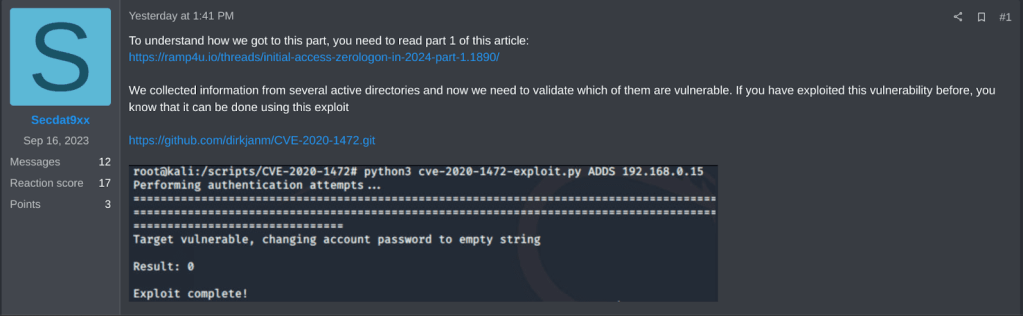
Source: Zero Fox Intelligence
While ZeroLogOn has been remediated with patches from Microsoft several years ago, it continues to be used as a method for threat actors to gain increased access and elevate privileges once they’ve gained an initial foothold within a domain. ZeroLogon has been used in the past as a method to assist in the deployment of ransomware, and I’m sure cybercriminals will continue to use similar methods in the future.
While Kairos is a smaller actor in the space, only targeting small and medium businesses with data extortion, the group’s tactics and rapid emergence signal a broader trend in the cybersecurity threat landscape. I’m sure the lucrative appeal of a large ROI with a relatively low investment are spurring the rise of more extortion groups (several hundreds of dollars for VPS, exfiltration tools, and the odd initial access purchase). IABs and access to forums like RAMP and XSS may help lower the barrier to entry for cybercriminals, and it appears that no business is too small to become a target.

